We are proud to announce Topicus KeyHub 30. This release is brimming with connectivity and integration features. An alpha version of a new provisioning protocol will be supported, namely SCIM. We are further expanding our provisioning configuration by allowing a provisioned system to be split up into different namespaces. Furthermore, this release will include a new version of our Terraform SDK and improvements to the corresponding OpenAPI specification. And not to forget, a good number of assorted improvements and bug fixes.
SCIM
TKH-1814 KeyHub now supports provisioning through the System for Cross-domain Identity Management, or SCIM. SCIM is an open standard that enables the automated provisioning of users and groups through a REST API. Due to the open nature of the specification, it is necessary to select the vendor that receives the SCIM provisioning so that KeyHub can use the correct dialect For this alpha version, we include three SCIM dialects: Amazon Web Services, Keystone, and a default implementation of RFC-7643 and RFC-7644.
We plan to support more dialects in future releases and make adjustments based on feedback.
Namespaces
TKH-2524 TKH-2617 TKH-2618 TKH-2622 TKH-2629 TKH-2636 TKH-2663 A namespace is a variant of an existing provisioned system with its own provisioning. With a namespace you can carve out a piece of an existing provisioned system, such as an organizational unit in LDAP/AD terms, and treat it as a separate provisioned system with separate owner and content administrator groups and its own groups on system and service accounts.
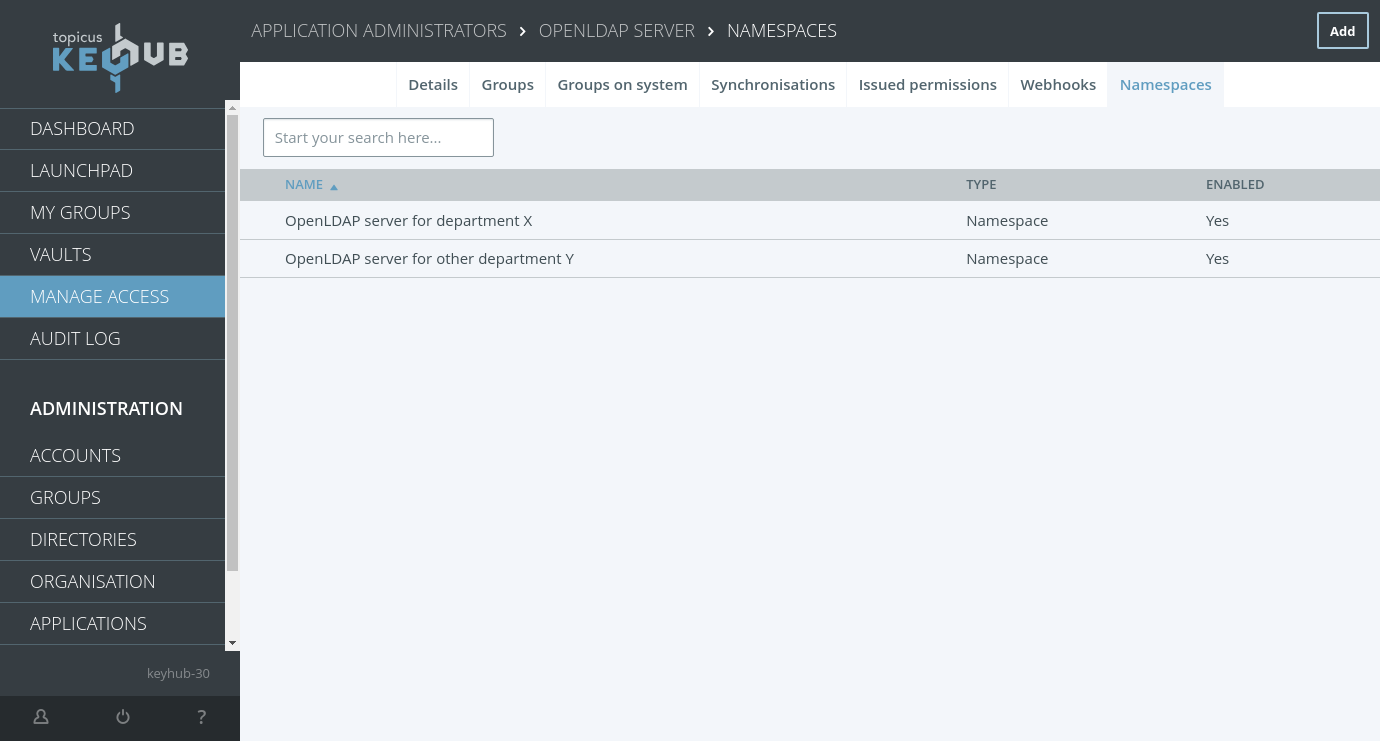
A namespace will use the connections and user accounts from the base system, while it has its own separate group and service account RDNs. A namespace can be linked to a different KeyHub organizational unit from the base system, if said organizational unit is below the base system's.
A namespace is functionally equivalent with a separate provisioned system on the same external system as an existing base system and for most users it will be indistinguishable from a 'normal' provisioned system.
Terraform Provider
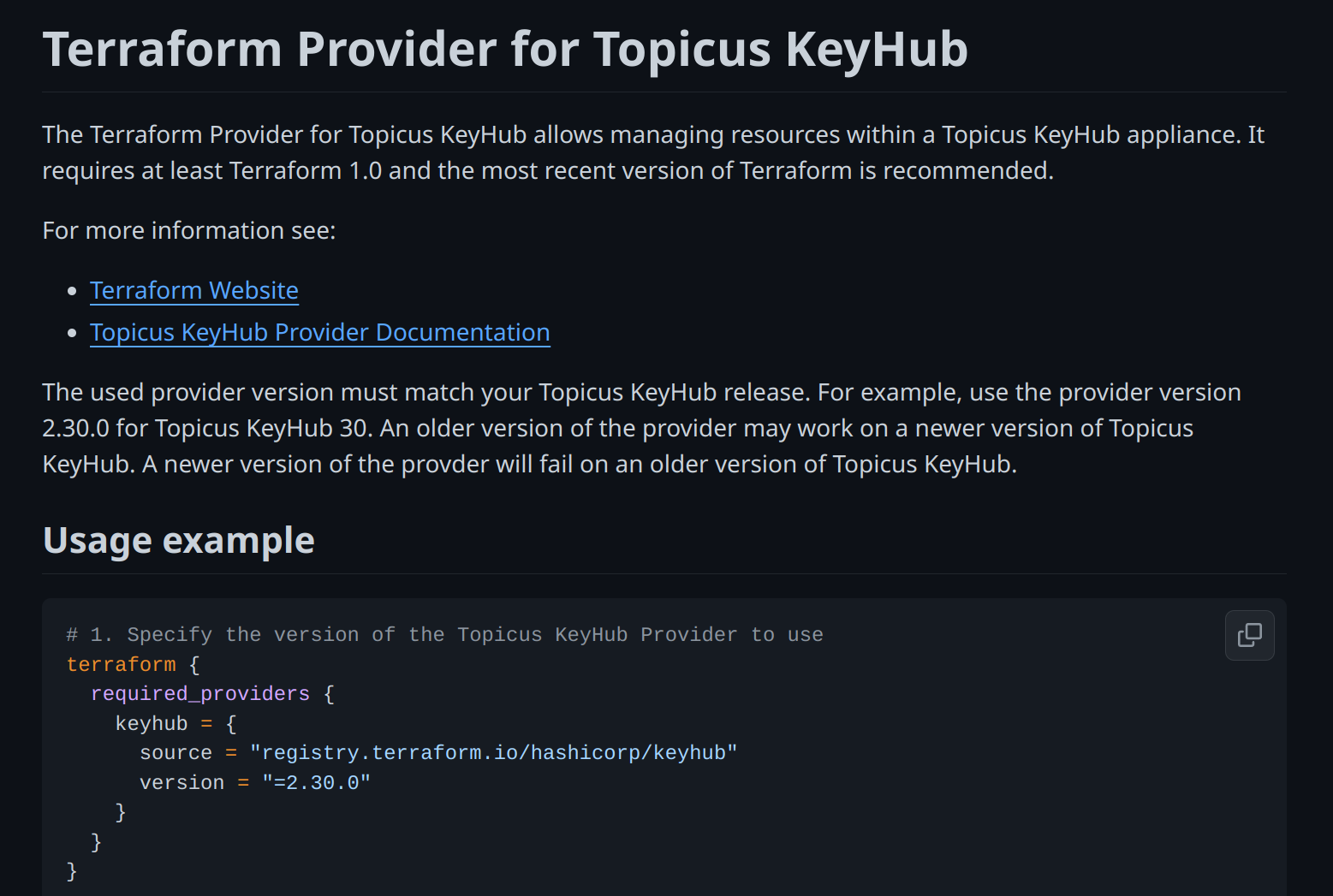
TKH-2611 We've had a Terraform Provider for some time now, but with Topicus KeyHub 30, we've released a whole new generation of the provider. This provider supports many more data sources, resources and attributes. The provider is built on top of our new Golang SDK and generated directly from our OpenAPI specification. This will ensure it will stay up to date with the latest features in Topicus KeyHub.
Assorted improvements
The following larger and smaller improvements and bug fixes were made:
-
TKH-2580You can now revoke access to a group on system if you are the owner. -
TKH-2605We have elevated the password encryption. -
TKH-2607Don't automatically send activation mail after approval of internal account creation. -
TKH-2608Technical dependency upgrade of OpenSAML to version 5. -
TKH-2609Prevented a double treat in queries that could result in a hibernate exception. -
TKH-2612Fixed a failed lock on a keystore from the filesystem. -
TKH-2613TKH-2614Filtering the account on their directories, and then on the directory's base-ou meant the directoryfilter's permissionchecks came into play, and non-keyhubadmins don't normally have permissions for directories. By avoiding the directoryfilter and adding a filterproperty directly for the account's base-ou we avoid any in-between permission checks. -
TKH-2615Removal of duplicated internal service. -
TKH-2626We no longer show the organization units you are not the owner of. -
TKH-2628Corrected a textual mistake in the grant application permission modification request. -
TKH-2631Calls on the infinispan cache are no longer blocking and are now purged correctly. -
TKH-2632Reduced the timeout on the EJB-pools to prevent an application deadlock. -
TKH-2633Made the provisioning logic more modular when provisioning multiple systems for one account. An error in one of these tasks should not stop the provisioning for the others. -
TKH-2634Referrences to shared secret are cleared before removal. -
TKH-2637KeyHub now uses the RFC-7919 dhparams. -
TKH-2638The remove button for the root organization unit is no longer visible. -
TKH-2639Updated the install license. -
TKH-2641We no longer cache downloaded log files. -
TKH-2647The request for transferring the ownership of a group on system will now be redirected to the correct organization unit. -
TKH-2650Upgrade of our application web server to WildFly 30.0.0. -
TKH-2656An add group admin request will now use the provided key if present. This should improve ease of use in automating these requests. -
TKH-2665An error in the key rotation was fixed that could cause problems at login. -
TKH-2670Provisioning on Microsoft Azure now correctly handles nested groups.

