We are proud to announce Topicus KeyHub 25. This release brings a great number of enhancements to integrations with other systems. Also, we've started with the phased rollout of organisational units. This exciting new feature will bring a lot of flexibility in the configuration of Topicus KeyHub for larger organisations. As usual, a number of assorted smaller changes and bug fixes are also included.
Important notice: corrupted vault recovery keys
TKH-2248 An error was discovered in the code responsible for upgrading vaults to newer encryption algorithms. In this process, the recovery key was not correctly updated, making recovery impossible for these vaults. We've corrected the error and the update to Topicus KeyHub 25 will reset all unusable vault recovery keys. These keys will be reconstructed automatically when users login. For vaults that had the recovery key reset, a warning will be displayed on the auditor dashboard until it has been reconstructed.
Provisioning and directories
This releases brings several enhancements to the provisioning and directory implementations. These enhancements will improve the stability and reliability of these integrations.
-
TKH-1675Directory status and metrics are now available through our OpenMetrics endpoint. -
TKH-1669The provisioning implementations now use a circuit breaker to prevent cascading failures due to a single broken system. -
TKH-1918TKH-2419It is now possible to remove a group from a linked system when the group is not empty. -
TKH-1980Provisioning now always requires 2FA.
-
TKH-2228The caching for provisioning was made more robust in case of communication errors with the linked system. -
TKH-2427Handling and reporting of errors with LDAP servers with a configured failover host, both linked systems and directories, was improved substantially.
OAuth 2.0 and OpenID Connect
We continuously work on the interoperability and security of our OAuth 2.0 and OpenID Connect implementation. This release contains two important changes in this area.
-
TKH-1949Topicus KeyHub now supports the OAuth 2.0 Form Post Response Mode for authorization requests. We've found that some libraries prefer this mode. This should make integrating with these libraries a lot easier. -
TKH-2112We've switched to encrypted access tokens. This will prevent leakage of information through these tokens. Keep in mind that tokens are issued with the Topicus KeyHub API as the default audience. If you wish to use tokens for a third-party API, you should request the tokens for that specific resource using a resource indicator. These tokens will not be encrypted and continue to follow the JSON Web Token (JWT) Profile for OAuth 2.0 Access Tokens.
Organisational units
TKH-2394 TKH-2396 This release contains the first steps for entirely new and exiting feature: organisational units. These will allow a Topicus KeyHub installation to be divided into separate parts, with separate groups and accounts. Users will only be able to see those parts of the organisation units they are part of. Topicus KeyHub 25 only contains the very first parts: the ability to create new organisational units. In the upcoming releases we will continue to expand this functionality.
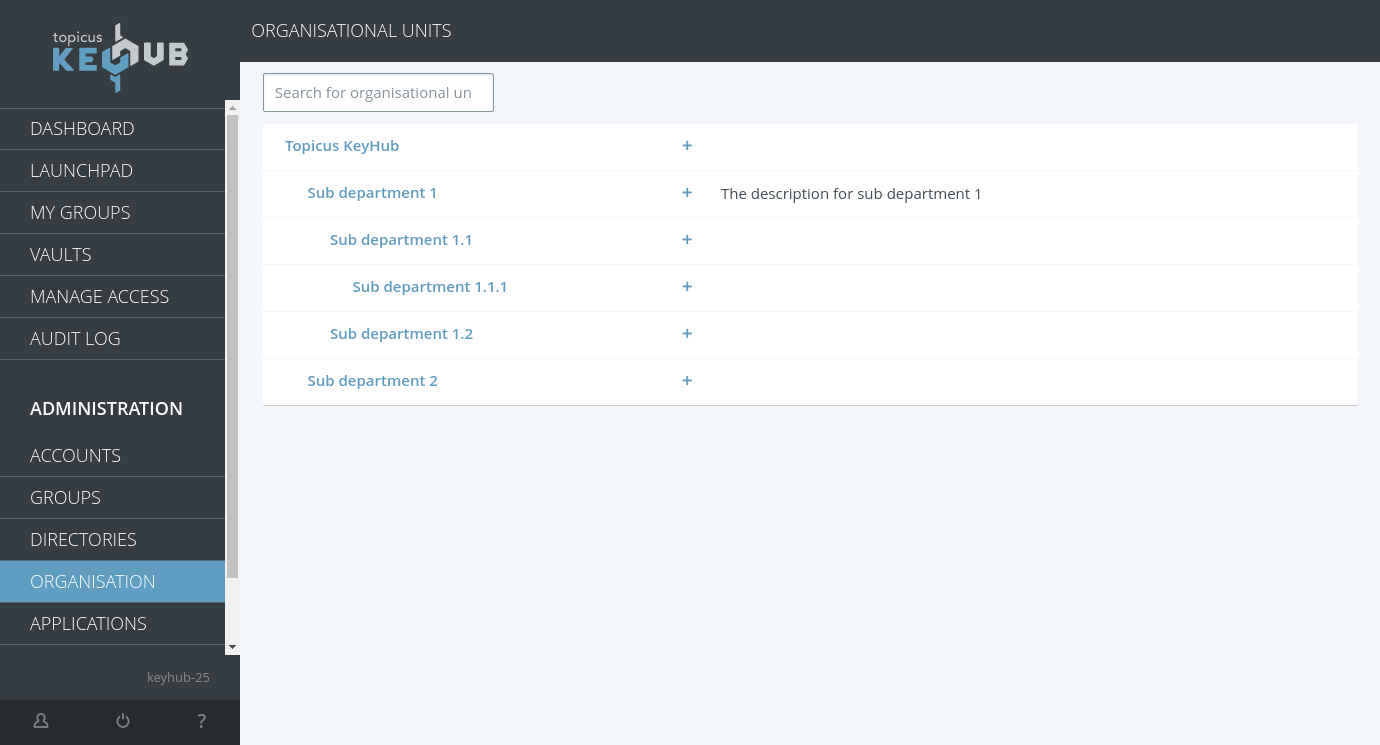
Organisational units
Small improvements
The following smaller improvements and bug fixes were made:
-
TKH-1131The SAML 2 metadata on applications is now validated and checked for consistency when saving the application. -
TKH-1206Several tests were added for SSO and OAuth2 flows. -
TKH-1728A notification is now displayed on the dashboard when the Topicus KeyHub installation has not been updated for a long time. -
TKH-1899Better feedback is provided to the user when trying to remove a KeyHub Administrator in a cleanup action. -
TKH-2103Clicking on the logo in the top left corner brings you to the about page. -
TKH-2146Tests were added for recovery of incorrect settings during a backup recovery. -
TKH-2160Changing configuration on group nesting or authorization now emits audit records. -
TKH-2178The syslog configuration was updated to make use of the latest features of rsyslogd. -
TKH-2208Users can now terminate all sessions with a single click on a button. -
TKH-2236The tests were updated to Groovy 4. -
TKH-2245OAuth2 clients can now assign any group for technical administration of newly created applications. -
TKH-2308The best practice guides were moved to our knowledge base. -
TKH-2323A notice is now displayed to users logging in on the terminal via SSH. -
TKH-2331When performing a database recovery, the number of audit records in a database in the past 2 weeks is now also displayed. This gives the administrator more information to pick the correct database as the new primary. -
TKH-2336A warning is now displayed when performing an offline update of a clustered install to always update one release at a time. -
TKH-2346Our build environment was updated to VirtualBox 7. -
TKH-2356The contents of mails, messages and notifications for requests was simplified to reduce the number of translations needed and make the texts more uniform. -
TKH-2357It is no longer possible to change a global trusted certificate when it is in use. -
TKH-2375When changing the password, other sessions are now terminated by default. -
TKH-2385Changes were made to support deployment from the AWS marketplace. -
TKH-2387Sorting groups on the auditor dashboard on the number of members now works as expected. -
TKH-2388Nested groups are now displayed in alphabetical order. -
TKH-2393A new donut was added to the account dashboard to display the status of 2FA for all users. -
TKH-2399Memory allocation of the appliance can now be configured. -
TKH-2404An error was fixed when trying to create an internal LDAP using the add button in the top-right corner. -
TKH-2406An error was fixed when sharing a vault record that was opened from the dashboard. -
TKH-2407An error was fixed on the dashboard that prevented the usage of the back button in some cases. -
TKH-2410The appliance manager now uses a much shorter timeout for calls to the KeyHub backend to prevent locking the user interface in some cases. -
TKH-2411Unparseable user agent strings are no longer reported as hacker. -
TKH-2414Error handling was improved when trying to use an invalid license. -
TKH-2415TKH-2422TKH-2426Several permission related errors were fixed when working with service accounts. In several cases the required permissions were missing, causing errors when opening pages or performing certain actions. -
TKH-2416An error was fixed when trying to perform a password reset for a non-existent account. -
TKH-2417Generation of mails was fixed when no feedback was given. -
TKH-2420An error was fixed on the token endpoint when trying to use previously invalidated tokens. -
TKH-2421An error was fixed that could cause invalid group membership signatures for KeyHub Administrators. -
TKH-2423Password recovery shares are now deleted when a user resets his/her vault. -
TKH-2425An error was fixed when trying to reinitialize pages, which could happen when using action links as bookmarks. -
TKH-2429The user feedback on copy actions in the vault was improved significantly. The icon is now toggled to a check mark, without hiding all other fields. -
TKH-2430Some requests where erroneously accepted automatically when issued by the KeyHub maintenance administrator. -
TKH-2432The order of configuration roll-out when re-enabling nodes in a cluster was changed to improve reliability. -
TKH-2440An error on the dashboard for service accounts was fixed when no linked systems existed yet. -
TKH-2441An error was fixed in the id_token validation that prevented SP initiated logout for legacy subject identifiers.

