We are proud to announce Topicus KeyHub 21. This release brings provisioning of service accounts on Active Directory. We've also greatly improved the UI (user interface) of our browser extension. Last, but not least, we've done a major overhaul of the encryption used by the Topicus KeyHub vaults. As usual, a number of assorted smaller changes and bug fixes are included.
Issues with the ELRepo repository
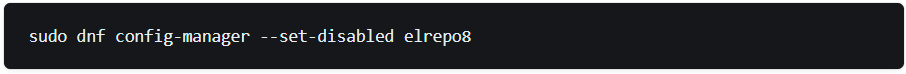
TKH-2051 The ELRepo repository is currently experiencing problems due to a DDoS attack. This can cause timeouts during an online upgrade of Topicus KeyHub. Starting with 21, we now serve all RPMs from our own mirror. To prevent issues during the upgrade, it is recommended to temporarily disable the ELRepo repository. It will be re-enabled and moved to our own mirror during the upgrade. Login on the appliance via ssh on port 50022 with the user keyhub and the maintenance password and type the following command:
New version number
Starting with Topicus KeyHub 21, we will switch to a new version numbering scheme. From now on, we will increase the major version number on every release and drop the minor version number. This new scheme corresponds better to how we already built releases. It also makes it easier to communicate about releases. This change only affects the version number, nothing else. You can still expect the same quality of our releases.
Browser extension
Several long-awaited improvements for the browser extensions have been implemented. Some of these target the extension itself, while other improvements were made to Topicus KeyHub itself to better guide the user in using the extension.
TKH-744TKH-2166A notification is shown on the dashboard if the browser extension is not installed or linked. This notification can be dismissed if the user does not want to install the extension.TKH-1427The link to add a new record has been added to the pop-up of the extension for easier access.TKH-1474It is now possible to search for records directly in the pop-up.TKH-1764An explicit click target was added to fill a TOTP code.TKH-1824Clicking on the name of a record now opens the URL. To edit a record a dedicated edit link was added.
Service accounts
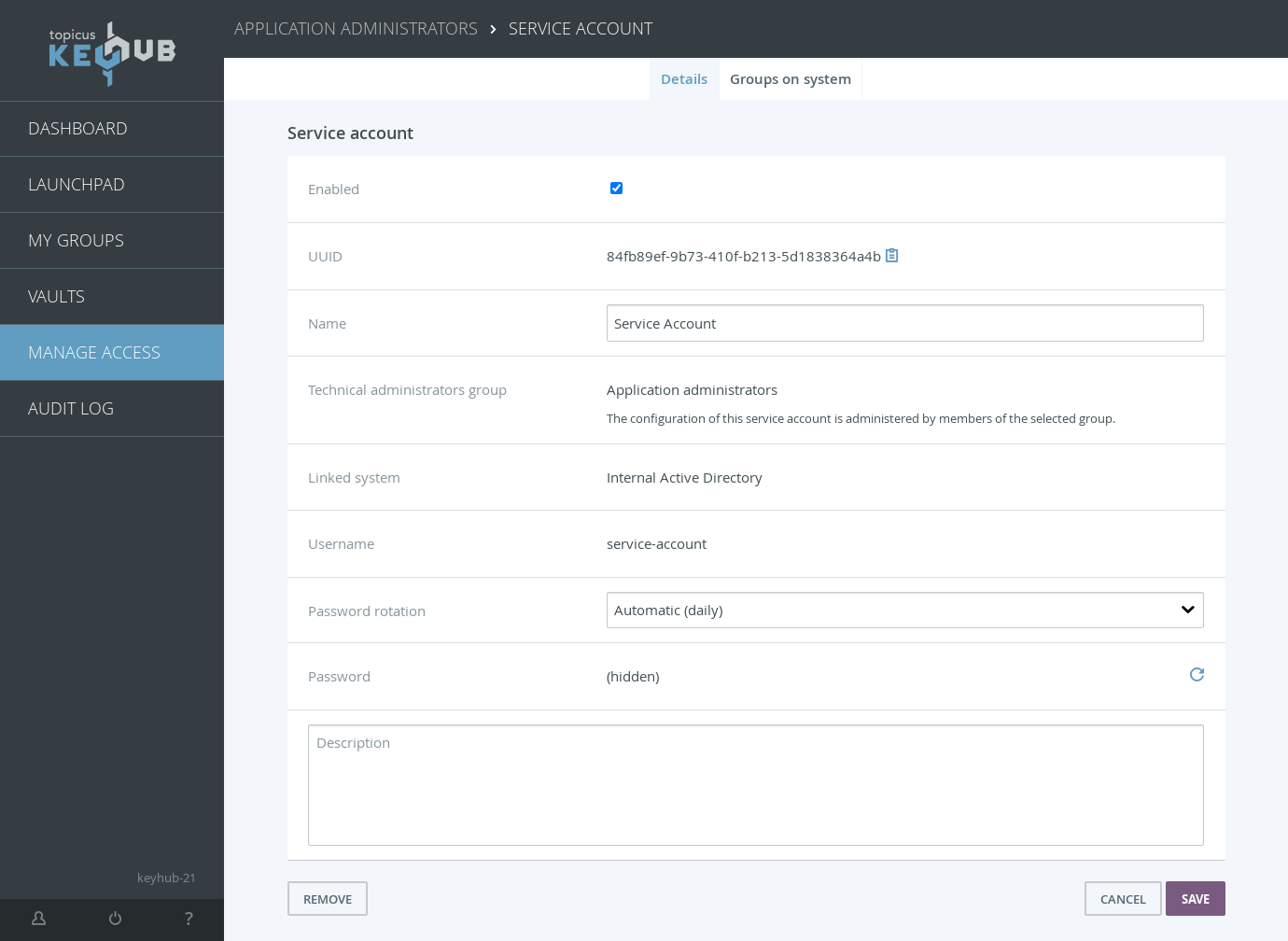
TKH-1982 TKH-2191 TKH-2192 TKH-2195 Topicus KeyHub 21 introduces service accounts. A service account is a non-personal account that can be used for automated services. These accounts are managed by a group in Topicus KeyHub and can be assigned groups on the provisioned system to give them the required permissions on the system. KeyHub can rotate the password for a service account automatically and share it in the vault. At the moment service accounts are only supported on Active Directory, but OpenLDAP and Azure will be supported in upcoming releases.
Cryptography
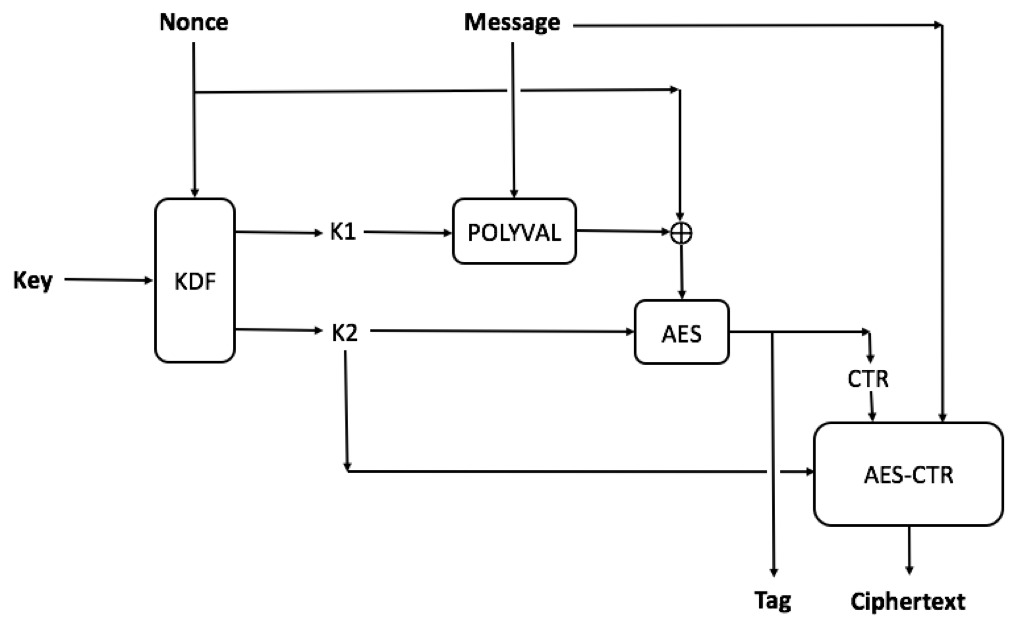
TKH-2057 TKH-2241 We've completely revised our encryption of the vaults. For symmetric encryption we switched from AES-256 with CBC to AES-256 with GCM-SIV. This offers protection against potential padding oracle attacks while also providing higher performance. Our asymmetric encryption scheme was still based on RSA with 4096 bit keys. While still considered secure, it suffers from similar padding oracle attacks, very low performance and large keys. We now use ECIES on the secp521r1 curve. This is a hybrid encryption scheme, offering the benefits of asymmetric encryption at the speed of symmetric encryption. It also addresses the potential padding oracle attack. All vaults will be re-encrypted using the new schemes automatically in the background.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-1992Docker compose was upgraded to 2.10.2.TKH-2051All RPMs are now served from our own mirror.TKH-2108It is now possible to configure provisioning to automatically remove unknown accounts.TKH-2157Certain cascading deletes could cause an error when deleting an account.TKH-2168Support for CentOS 7 was removed from the rpm.TKH-2171Some code that was deprecated in the previous version has now been removed.TKH-2177Audit records for updates on webhooks now contain all relevant context information.TKH-2183TKH-2221After restoring a backup, the appliance manager did not reload its secrets from the restored files. This caused issues with SSO and prevented setting up a cluster.TKH-2206The vault initialization code was simplified drastically after implementing the new encryption schemes.TKH-2207Invoking multiple simultaneous requests is now much less likely to trigger concurrent modification errors.TKH-2209TKH-2210Virtualbox in our buildsystem was upgraded to the latest version.TKH-2211The dashboard layout page now shows all groups, even if the account is member of over 100 groups.TKH-2215Deployment of a new VM on Azure was fixed.TKH-2216In an offline installation, some AlmaLinux repositories could get enabled during an upgrade.TKH-2220Drivers for VirtIO were added to the initramfs to allow booting on KVM.TKH-2224Some concurrency issues were fixed that could trigger an error in the appliance manager while restoring a backup.TKH-2225It is now possible to select a different message template for forwarded syslog messages.TKH-2234An error was fixed that could cause the synchronization on LDAP to crash.

