We're proud to announce Topicus KeyHub 19.2, in which we added a new dashboard for auditing accounts. We also added a new workflow for reviewing audits. Dynamic account provisioning has seen many improvements regarding performance, metrics and logging information. As usual, a large number of smaller changes and bug fixes are included.
Important notice: Upgrading a self-hosted docker deployment
For users of our virtual appliance the following steps will be automated, however if you run Topicus KeyHub as a self-hosted docker deployment, the update to 19.2 requires some additional actions.
An additional secret must be added as property in the env-file, as it is required for the solution to TKH-1888. This secret is best generated using a strong secret generator, such as the password generator in the Topicus KeyHub vault. The exact value does not matter, but it must be URL safe (the passwords generated by the vault are URL safe). The secret is:
ENCRYPTION_SECRET={secret here}Account dashboard for auditors
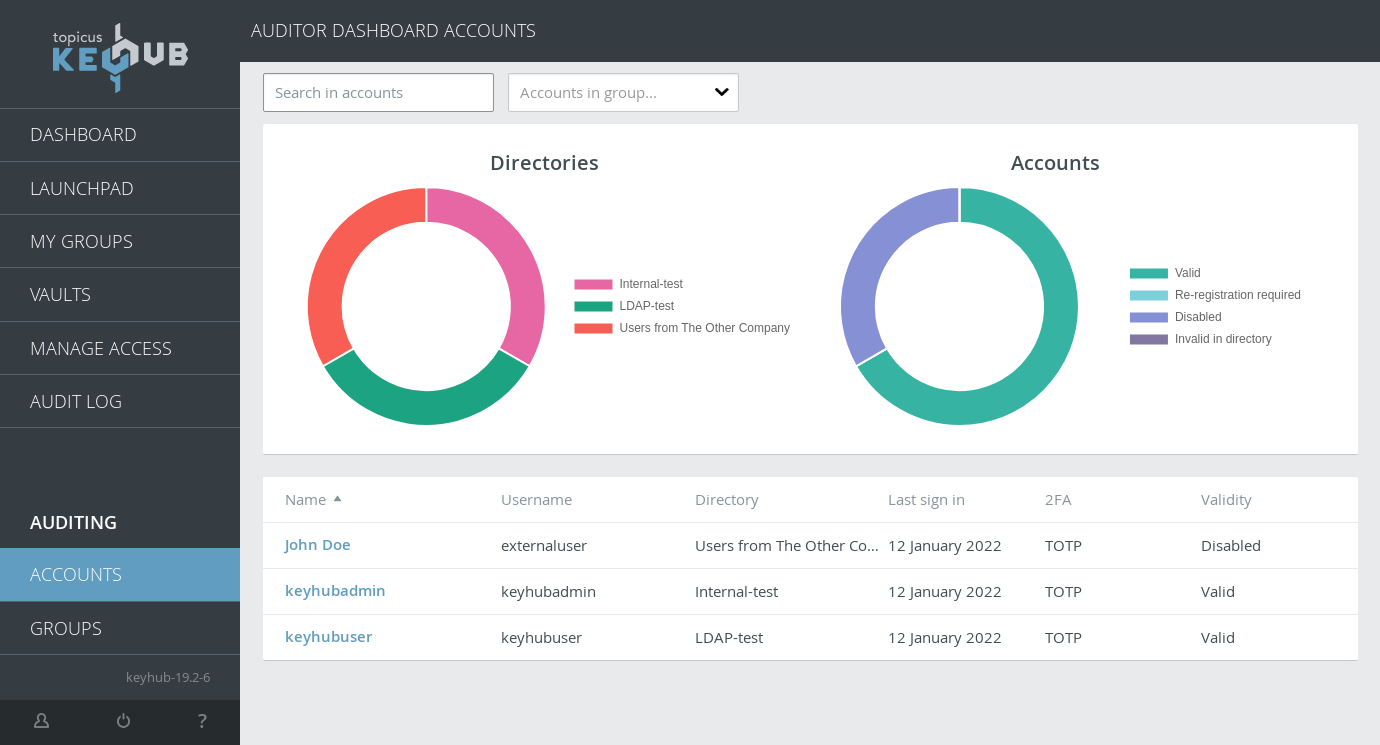
TKH-1050 TKH-2000 A completely new account dashboard was added for auditors. This dashboard displays all accounts with status information. Detailed information for accounts can be acquired by clicking on an account.
Auditing workflow enhancements
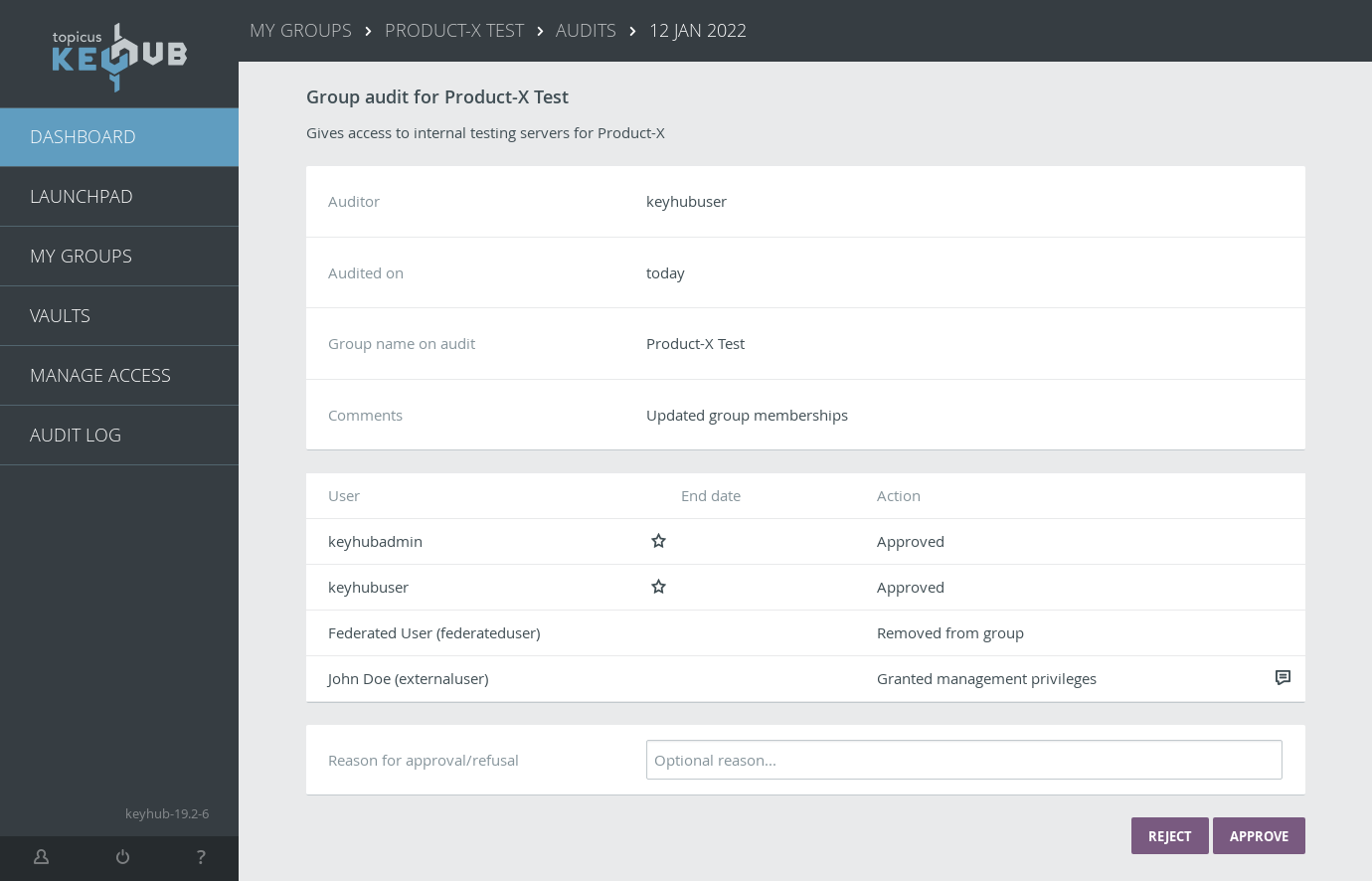
TKH-1351 TKH-1752 TKH-1952 TKH-1999 It is now possible to require that audits on a group be reviewed by members of a different group. This allows the audits of groups to be performed decentralized by the group's managers, while maintaining centralized control. Additionally, an auditor can now request a group to be audited immediately, rather than waiting for the next periodic audit.
Account provisioning
Significant improvements were made to the account provisioning subsystems of Topicus KeyHub. These improvements greatly increase the reliability, performance and aid in troubleshooting potential problems.
TKH-1333Detailed logs are now kept for every full synchronization of a linked system. These logs can be viewed directly from Topicus KeyHub. It is also possible to manually trigger a full synchronization for a system.TKH-1499The OpenMetrics endpoint now contains detailed metrics of all interactions with linked systems, reporting the number of calls, the duration of those calls and counts on errors.TKH-1935A sophisticated caching layer was added to all provisioning implementations, greatly reducing the number of calls needed for synchronization.TKH-1984TKH-1985Updates on provisioned accounts are now only performed when needed, containing only the changed values, rather than overwriting all values on every synchronization.TKH-1989A bug was fixed in Azure provisioning when using username prefixes.
OpenAPI definition
TKH-1988 We've put a lot of effort in expanding our OpenAPI definition. All available endpoints are documented now with comprehensive examples of payloads and descriptions of the available query parameters. The OpenAPI definition is now also validated during our build process to prevent regressions in the future.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-1342The best practice guide now describes importing the OVA in vSphere.TKH-1479The groups auditor dashboard now allows exporting the displayed groups to CSV.TKH-1577A cluster can now be configured to automatically disable nodes that are not part of the quorum.TKH-1605The Selenium test stack has been upgraded to Selenium 4.TKH-1767OIDC directories can now send alogin_hintparameter on login to help pre-select the authenticating user.TKH-1794An error was fixed in the calculation of the padding of keys used for social recovery which would cause the recovery to fail for 1 out of 256 keys.TKH-1800Viewing log files in the appliance manager now only displays the last 5mb. Compressed files can also be viewed this way.TKH-1846A section about the audit log was added to the manual.TKH-1860It is now possible to display a maintenance message to all users on all pages.TKH-1888Encrypted fields (other than vault records) in the database are now encrypted using a key bound to a single installation.TKH-1895OpenSAML and Pac4j were upgraded to the next major versions: 4.1 and 5.2 respectively.TKH-1922The docker containers used for tests were upgraded to the latest, Selenium 4 based, versions.TKH-1930Support for OAuth1 has been removed.TKH-1943SaltStack no longer logs the content of changes to most managed files to prevent leaking sensitive information to the logs.TKH-1947It is now possible to get a warning about expired vault records 2 or 3 months in advance, in addition to the existing options of 2 weeks, 1 month or 6 months.TKH-1953A potential deadlock was fixed that could cause the appliance manager to get stuck during Salt calls.TKH-1960Disabled accounts are now correctly added to the counts on the groups auditor dashboard.TKH-1961The running dots animation in the appliance manager has been replaced by a more efficient CSS only implementation.TKH-1962TKH-2003The Java runtime has been upgraded to Java 17.TKH-1968The execution service in the appliance manager can now handle multiple tasks in serial, queuing subsequent scheduled tasks.TKH-1969The query to collect groups overdue for an audit was fixed to account for some corner cases.TKH-1971The message displayed when adding managers via the breaking glass protocol has been improved.TKH-1973Many small fixes were made in the manual.TKH-1976E-mails to group managers are no longer sent to KeyHub administrators when a single manager of a group tries to send an e-mail to themselves.TKH-1979Additional audit log entries were added for some authentication stages.TKH-1983The URLs for vault records were changed in a previous release. The browser extension now uses the new scheme to open records.TKH-1990An audit log entry was added when a user changes his/her SSH public key.TKH-1991Password synchronization is automatically enabled when Topicus KeyHub detects that the directory password is equal to the password used for KeyHub.TKH-1993The messages displayed to users for 2FA have been adjusted to account for hardware TOTP tokens.TKH-1995Audit log entries for authentication stages now contain the IP address of the user.TKH-2005A potential error was fixed when requesting updates to group memberships when authorized by a different group.

