We're proud to announce KeyHub 19.0, which includes a number of long wished for features. It is now possible to read account attributes from an account directory and use these when provisioning to a linked system or to a SAML- or OIDC-client. In addition, members of the auditor group can now create custom classifications for KeyHub groups to aid them in their work. We also hardened our login page against bots to further our security.
Reading and using custom attributes for accounts
TKH-1218 TKH-1649 TKH-1700 TKH-1876 TKH-1877 It is now possible to read extra attributes from an account directory (OIDC or LDAP) and save them with the account. These attributes can then be used in custom attribute scripts for client such as OIDC applications. Additionally, we implemented custom attributes for linked systems, such as ADs and LDAPs. Combined this means you can now provision an account to a target AD with a set of custom attributes based (whole or in part) on the attributes read from the source AD.
Classifying groups
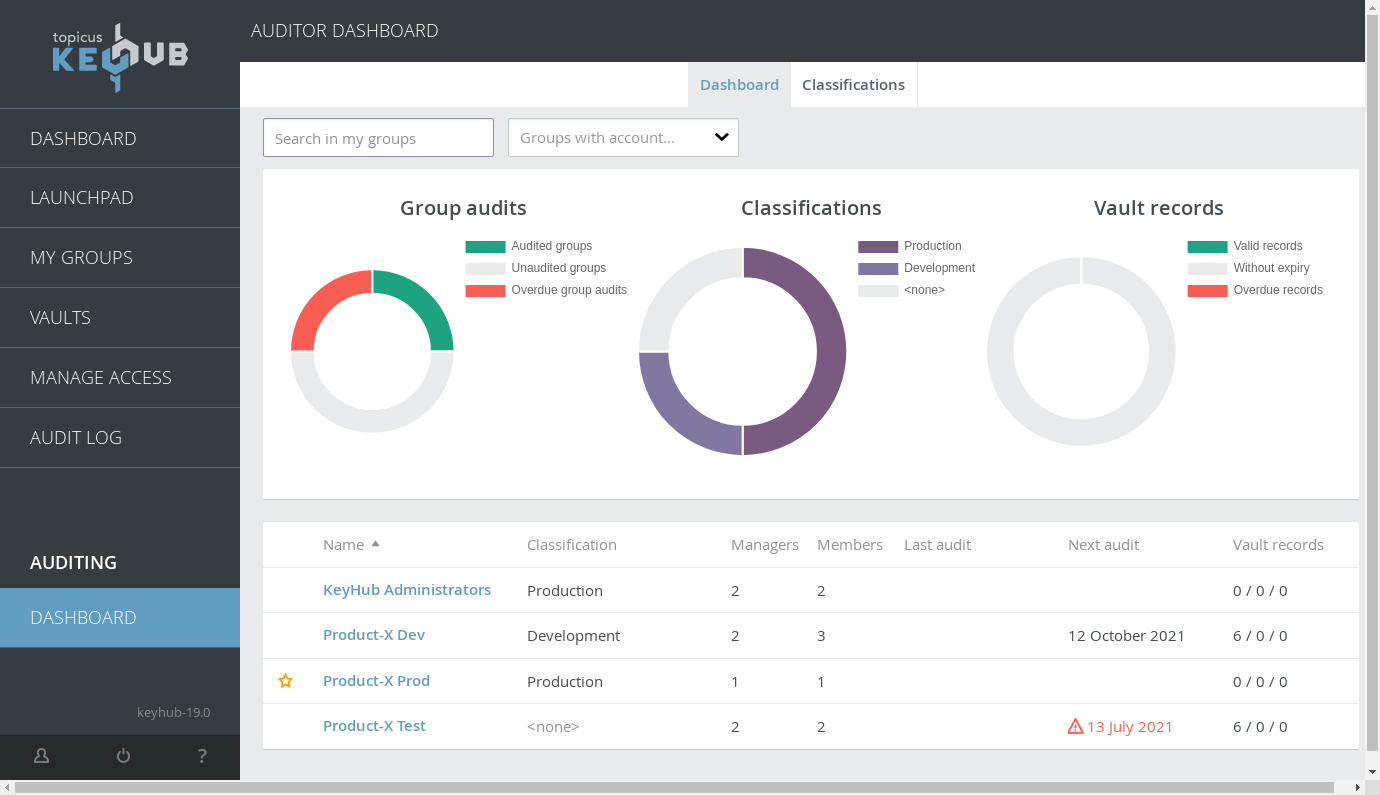
TKH-1480 TKH-1481 TKH-1482 Members of the auditor group can now create classifications and add them to groups. These classifications are visible on the auditor dashboard and can then be filtered and sorted on.
Additionally, we consolidated some columns on the auditor dashboard to make room for the new column and changed it so most columns can also be sorted on. We also split up some of the warning icons so there are more specific icons for specific warnings.
Bot protection
TKH-1806 TKH-1879 Our loginpage is now hardened against bot users. A Proof-of-Work-algorithm is used to prevent and/or slow down automated logins to lower the feasibility of attacks.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-1504The KeyHub CLI now tries to open the system default browser for authorization when logging in on behalf of a user.TKH-1568We added functionality to detect and (automatically) compensate for time drift with offline TOTP-devices, such as certain hardtokens.TKH-1685There's now an option to restart all Pgpool instances across the cluster. This can sometimes be the easiest way to resolve a cluster problem.TKH-1722The group details page now contains a list of all groups for which this group performs any kind of authorization, be that for activation or group membership.TKH-1734The appliance manager's pages should now be more resistant to restarts. The page should no longer "hang" while updating KeyHub.TKH-1740Audit records for actions triggered by accepting a request in most cases now show the requester, instead of the approver, as the one performing the triggered action. This resolves issues where this could lead to confusing situations.TKH-1755KeyHub now hooks into Azure snapshot flow so that every snapshot contains a fresh KeyHub backup.TKH-1760The timeout of KeyHub sessions can now be configured.TKH-1770KeyHub now attempts to strip the domain from the username, to better facilitate users who are used to logging with a username like 'user@company.com'.TKH-1776TKH-1855The KeyHub appliance now fully supports KVM with virtIO. In addition, we built in support for AWS's HVM.TKH-1780The account cleanup default selection is now only the inactive accounts, instead of all accounts.TKH-1804Internal accounts without a filled 'company' attribute should now once again receive their registration mails.TKH-1807An error during provisioning should lead to the "config required" notification staying on the user's dashboard.TKH-1805TKH-1809The algorithm that automatically cleans up unused provisioned accounts from the linked system has been improved. KeyHub now only cleans up accounts on a linked system if the corresponding KeyHub account has not had any connection to said system for more than two weeks.TKH-1810We have upgraded WildFly to version 24.TKH-1811We upgraded several Javascript libraries used in our browser extension to a newer major version and/or a supported alternative.TKH-1812Pgpool was upgraded to 4.2.4.TKH-1815KeyHub now supports OAuth 2.0 Resource Indicators (RFC-8707). KeyHub uses these to offer a token exchange via the KeyHub CLI.TKH-1818Tokens provided to a OAuth 2.0/OIDC client on behalf of a user are revoked when the user no longer has access to the client.TKH-1820Rebooting (as part of updating) can no longer fail silently and halt the update/reboot process.TKH-1821A cluster upgrade is now more resistant to its own reboot actions.TKH-1833You can now specify in an OAuth client's configuration that KeyHub's REST API should return full stacktraces for debugging purposes.TKH-1834An auditor group can now be private.TKH-1837The dashboard page should no longer crash for KeyHub admins when a user requests a 2FA reset. It should also now show the reset on the dashboards of the users who have to process it.TKH-1838Updating a cluster no longer results in incorrect e-mail notifications about errors in the snapshotting system.TKH-1840Generating self-signed certificates during installation should automatically turn off the Let's Encrypt option.TKH-1842The "check for updates" link in the appliance is no longer visible when running in offline mode, unless a company repo has been set. In that case it will change to "check for OS updates".TKH-1843Logging out on Azure from KeyHub should work once again.TKH-1844TKH-1856The text on the screens and in the manual related to password and 2FA resets has been updated to reflect the latest "social recovery" changes in the process in previous versions.TKH-1848The mail sent when a password reset request has been accepted should now contain the reason provided when accepting.TKH-1849We fixed a possible authentication loop that could occur when logging in after a long time in combination with a security key.TKH-1850KeyHub admins should once again be able to open the details of applications that have a Launchpad tile in all cases.TKH-1861Adding a new node to a cluster should no longer result in an error on the last step.TKH-1862Concurrent changes to authorizations and open requests no longer lead to errors.TKH-1863The option to configure authorization on membership is no longer visible to KeyHub administrators when they were not allowed to edit the group.TKH-1864It is no longer possible to submit requests on changes in group membership for your own account.TKH-1870When viewing your own account or that of the maintenance admin, the 2FA status is now correctly displayed.TKH-1873Inactive accounts no longer lead to errors while sending notification e-mails.

