We are proud to announce the 16.3 release of Topicus KeyHub. In this release we continued our efforts to further strengthen our application. Several new defensive measures were implemented. We therefore strongly recommend our users to upgrade to 16.3. As usual, a number of smaller improvements have been made and several issues have been fixed.
Important notice: Several security improvements
Topicus KeyHub 16.3 fixes several security issues identified during an independent security audit conducted by one of our customers. In addition, we further strengthened Topicus KeyHub using some new techniques, like Fetch Metadata Request Headers. Many of these features are made possible by Apache Wicket 9.
TKH-1337Topicus KeyHub now implements a very strict Content Security Policy. Nounsafedirectives are used and only local resources are allowed.TKH-1405When Fetch Metadata Request Headers are detected, these are now used to prevent CSRF attacks. These headers are already sent by all Chromium based browsers and we expect other browsers will follow. When the headers are not detected, Topicus KeyHub will fall back to the old, origin based CSRF detection.TKH-1451Wicket page instances kept on the server in the user's session are now encrypted with a session-bound key. This means that even when confidential information is included on a page, it will never be stored in plain text. Not even for the duration of a user's session.TKH-1452The command line interface now properly logs out on the server as well. It does so by revoking the access token it has using our newly introduced token revocation endpoint.
In addition to these more notable security improvements, the following smaller changes were made:
TKH-1449TheX-Content-Type-Optionsheader is set tonosniffto prevent content type detection.TKH-1450TheReferrer-Policyheader is set tostrict-origin-when-cross-originto prevent leakage of information on cross origin navigation.TKH-1453The select2 quick search drop down boxes now have much better input validation.TKH-1460Topicus KeyHub no longer follows aHostheader sent. Although no known way of abusing this exists, it may lead to spoofing attacks.TKH-1461TheStrict-Transport-Securityheader is now set to 1 year, following the recommendations.TKH-1463TheSameSiteattribute is set on all cookies.TKH-1472When editing a vault record, Topicus KeyHub will no longer present secrets when the page has not be used for over 15 minutes.
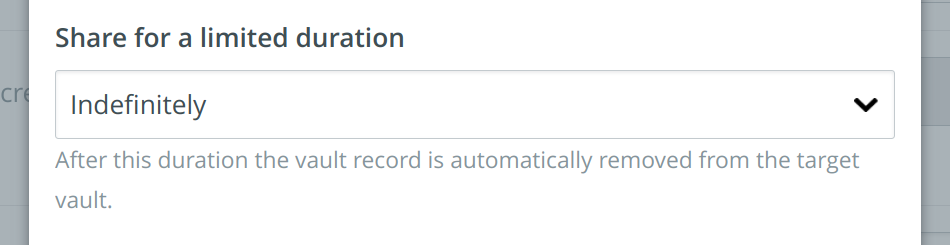
Sharing a vault record for a limited time period
TKH-1447 In Topicus KeyHub 15.0 we added support for moving, copying and sharing vault records between vaults. With this release, it is now possible to set an end time for a shared vault record. When the specified time has elapsed, the record will automatically be removed from the target vault.
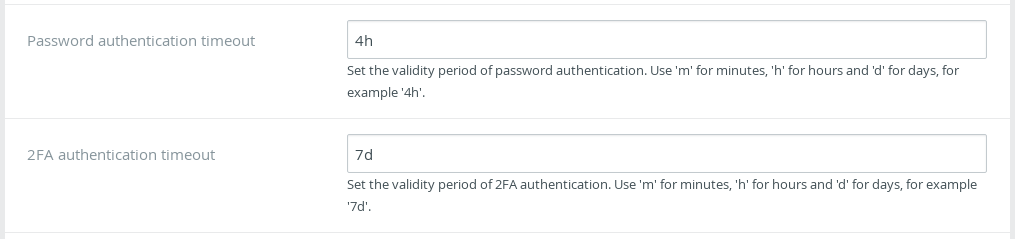
Configurable session timeouts
TKH-1471 For some organisations the default timeouts used by Topicus KeyHub may not be fitting. It is now possible to change both the validity period of a password authentication and a 2FA authentication.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-1448The VM in the Azure marketplace was updated to the latest version and some deployment issues were fixed.TKH-1454The Wicket page identifier in the URL had precedence over the path. This could result in users navigating to the wrong item when opening bookmarked URLs.TKH-1458A race condition during login could trigger a cascade of errors, sometimes leading to a failure of the HTTP connection pool of the Topicus KeyHub console.TKH-1459Manually added users within the appliance are now created in the range 2000 to 3000 to prevent collisions with managed users.TKH-1462The redirect fromhttp://tohttps://did not always work correctly. Users could get a 404.TKH-1464Passwords on provisioned Active Directories are now correctly updated, even when the account is currently inactive.TKH-1465Performance of the audit log has been improved by loading the log in smaller segments.TKH-1466Performance of the dashboard has been improved when a user has a very large number of notifications.TKH-1469The auditing information returned by the REST API for vault records was sometimes shuffled, causing the information for one record to be attached to another.TKH-1470The command line interface did not set the end date when creating new vault records when told to do so.TKH-1476Due to a rounding error, it was possible to enable a group for a period slightly longer than 12 hours. This could cause various rendering errors on the dashboard.TKH-1477Modification request parameters were not shown when a request was accepted via the link in the e-mail.TKH-1483An LDAP configured with nested organizations would lead to an error when trying to read the external UUID.TKH-1484It is now possible to have theSAM-Account-Nameon an AD filled with the truncated username when the (constructed) username does not fit. By default, Topicus KeyHub will leave it empty, causing the Active Directory to generate a random value. This might lead to unrecognizable account names for our users when an application relies onSAM-Account-Name.TKH-1485When a password change on an LDAP directory was detected during registration, the account could enter a non-recoverable state.TKH-1488A regression that broke SAML logins when prompted for 2FA was fixed in16.3-3.

