It has been almost 5 years since the very first commit, on September the 19th 2014, with which Topicus KeyHub was born. In these 5 years a lot has changed, but our focus remains the same. We continue to deliver an identity and access management solution that is very different from other the solutions in the market. Our flexible, group based, authorization is unparalleled and we will continue expanding Topicus KeyHub based on this vision.
Today, we are pleased to announce Topicus KeyHub 14.3. In this release we bring a first iteration of an OpenAPI documentation of our RESTful backend. Starting with 14.3, it is also possible to rename accounts or migrate accounts to another directory. As usual, a number of smaller improvements have been made and several issues have been fixed. Before upgrading to 14.3 be sure to read the following important notices.
Important notice: admin user renamed to keyhub
TKH-1238 When running Topicus KeyHub in maintenance mode, the username to login is now keyhub instead of admin. This is in line with the maintenance user of the appliance. If a user with the name keyhub already existed, the existing user is renamed to keyhub2.
OpenAPI documentation
TKH-1234 We have started documenting the Topicus KeyHub RESTful backend. With 14.3, all resources related to vaults and groups have been documented. You can find the OpenAPI documentation at the following URL: $HOSTNAME/keyhub/rest/v1/openapi.json. An openapi.yaml is also available. You can use this OpenAPI definition to generate a REST client or as a reference for the API. In future versions of Topicus KeyHub more resources will be documented. Please let us know which ones you would like to see!
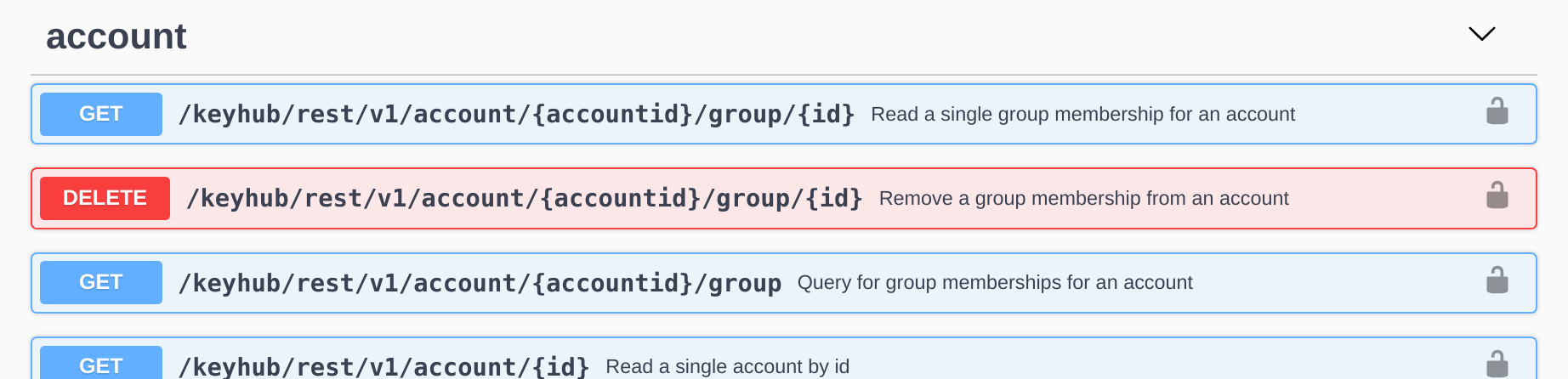
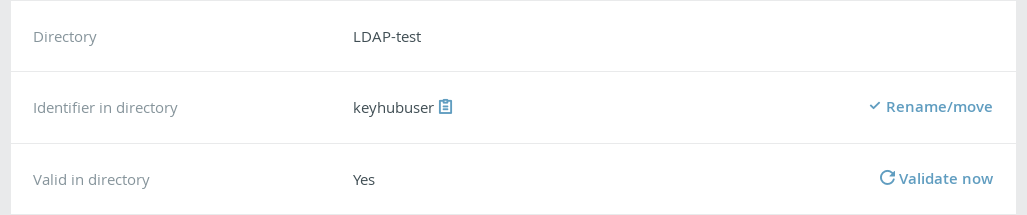
Renaming and moving accounts
TKH-629 Sometimes the identifying information for an account changes. For example, when a person gets married and decides to adopt the name of his or her partner this often results an a change of the DN in an LDAP directory. It is now possible to mark such an account for rename or even move it to another directory. Once marked, the user will have to perform a partial re-registration in which the account is linked to the new identifying information.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-677When Topicus KeyHub is starting, a meaningful message is shown to the users.TKH-616The signing certificated for the IdP can now be renewed.TKH-1183Performance of the application has been improved throughout the application and even more so for 'Manage access'.TKH-1199It is now possible to specify port ranges in the firewall settings.TKH-1202The appliance can now generate certificate chains automatically from a CA bundle.TKH-1212Error handling has been improved when navigating back and forth many times.TKH-1213Many resources on the Topicus KeyHub backend are now private to certain applications, preventing possible abuse.TKH-1214Usernames with brackets no longer cause problems for provisioning and authentication.TKH-1215Group names with brackets can now be used for provisioning.TKH-1216It is now possible to remove a record for a group on system from Topicus KeyHub without actually removing the group from the system.TKH-1219The e-mail password is no longer displayed when applying configuration changes.TKH-1221A redirection issue during login was fixed, which could cause a user with a valid session to still end up on the login screen.TKH-1222An error was fixed when enabling a group under certain conditions.TKH-1224Some textual changes were made throughout the application.TKH-1226Topicus KeyHub no longer restarts when the mail configuration is changed.TKH-1228The add button for application has been removed. Applications can now only be added via 'Manage access'.TKH-1229The appliance will now wait until a snapshot recovery has been completed before attempting to create a new snapshot.TKH-1230The error message when trying to create a group on an inactive system has been improved.TKH-1231Users can now view the audit log for groups they are member of.TKH-1232The application server was upgraded to WildFly 17.TKH-1233The user no longer gets an error at login when 2FA is disabled and an expired record exists in one of the vaults.TKH-1235Auditor permissions now require 2FA.TKH-1236A crash of the application was fixed when multiple users tried to login at exactly the same time, both with a Google push notification.TKH-1240A XSS attack was fixed in URLs in the vault.TKH-1241An incorrect check on the add audit button could cause it to be invisible.TKH-1251Fix conflict between RPM and PIP packages. Patched in 14.3-2.

