We are pleased to announce Topicus KeyHub 12.3. This release brings many improvements to our virtual appliance, IDP initiated SSO flows and a user manual in English. As usual, a large number of smaller improvements have been made and many issues have been fixed.
Important notices
Before upgrading to 12.3 be sure to read the following important notices. Some changes need to be made to your configuration or your upgrade will fail. Also, tightened security validations might impact your SSO applications.
Changes to docker-compose.yml
TKH-969 TKH-972 Starting with 12.3 we now push our docker containers to our own repository. This means you need to change the images in your docker-compose.yml. The repository does not require authentication. For keyhub-db use docker.topicus-keyhub.com/keyhub/keyhub-db and for keyhub-app use docker.topicus-keyhub.com/keyhub/keyhub-app. Also, a new container was added to perform custom attribute evaluation in a sandbox. Without this container, custom attributes on OAuth2 and SAML2 applications will not work. Add the following container to your docker-compose.yml:
scriptengine:
container_name: "keyhub-scriptengine"
image: docker.topicus-keyhub.com/keyhub/keyhub-scriptengine
restart: always
Finally, add this new container as a dependency to the keyhub-app container:
depends_on:
- db
- scriptengine
Naturally, if you are running the virtual appliance, this will all be handled as part of the regular upgrade.
Changes in callback URL validation
TKH-974 In accordance to the OAuth 2.0 Security recommendations Topicus KeyHub now strictly validates query parameter presence and contents in callback URLs. Before upgrading to 12.3, make sure your OAuth2/OIDC applications have their callback URLs correctly set, including any query parameters. The callback URL used by an application can be seen in the browser console as the redirect_uri query parameter for the request on the /login/oauth2/authorize endpoint. A mismatch in the callback URL will result in an error when trying to use the SSO application. Naturally, the simple wildcards in the hostname or path and the port ranges are still supported.
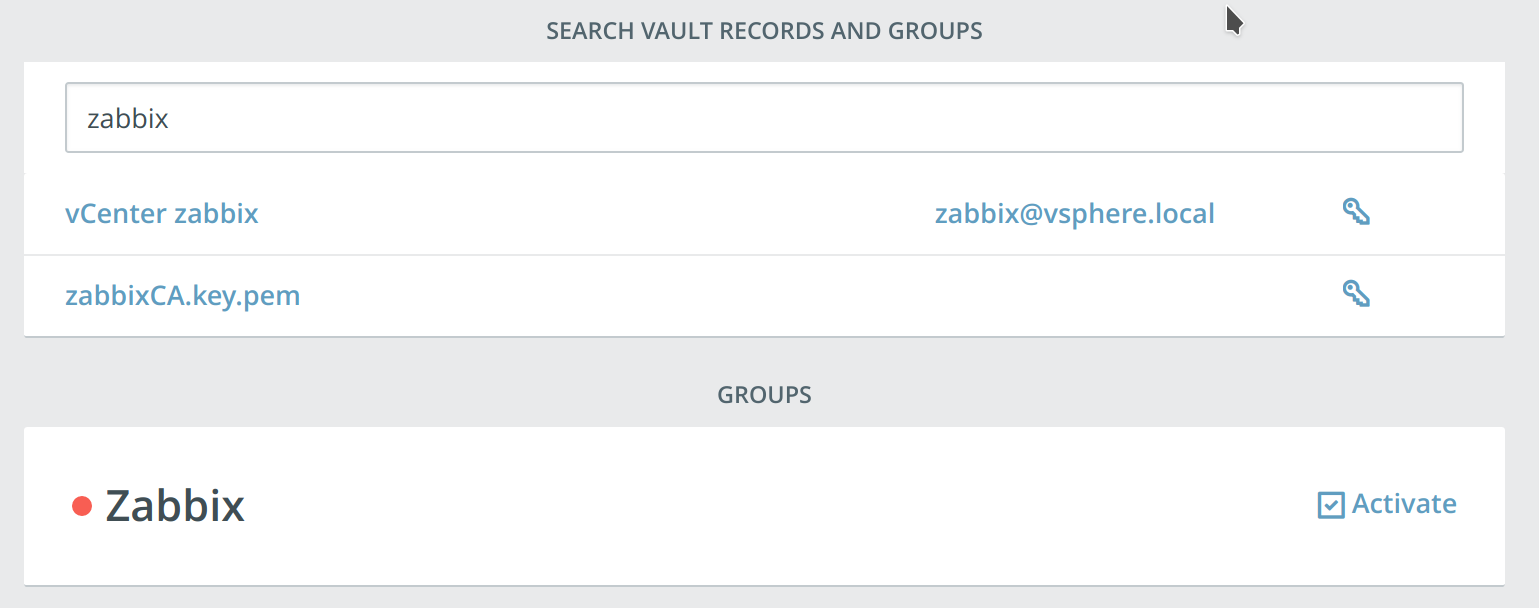
Search groups on your dashboard
TKH-992 The quick search field on the dashboard now also filters the groups on your dashboard. This allows you to quickly search vault records and groups at the same time.
IDP initiated flows for SAML and OIDC
TKH-985 A new endpoint for IDP initiated SAML and OIDC flows has been added. For example, https://keyhub.example.com/login/initiate?client=urn:amazon:webservices will redirect the user to Amazon. It is also possible to use the client identifier of an OIDC client, which will initiate the third party login flow using the configured Initiate login URI.
Group related audit log messages
TKH-1037 The audit log now shows all group related messages to all members of a group, not just the managers. This will give all members of the group insight in important events such as new members, changes to applications or modified vault records.
Virtual appliance
With our previous release we've introduced a new way to install Topicus KeyHub: a virtual appliance. This release vastly improves the installation via this virtual appliance and integrates the appliance manager with Topicus KeyHub itself. The following issues were solved:
TKH-769System and Topicus KeyHub upgrades are now performed by SaltStack execution modules.TKH-921OSS licenses are now distributed with the appliance in conformance to the license requirements.TKH-934The appliance manager can now create and restore backups.TKH-936The installation wizard now allows creating the first directory and user.TKH-937You can now configure Single Sign-on between Topicus KeyHub and the appliance manager.TKH-938Before applying new configuration, the appliance manager now shows the modified settings.TKH-955Tooling for Azure is now automatically installed when the virtual appliance runs on Azure.TKH-961TKH-980TKH-982TKH-983Code coverage of the test suite is now recorded and has been improved considerably.TKH-964The appliance manager now has a user manual.TKH-967The internet connectivity check now uses a more reliable target.TKH-989A system update could cause SaltStack to restart and the update to fail.TKH-1001The transfer of the user session during install has been made much more reliable.TKH-1002The recovery key that must be downloaded during install now has a descriptive name.TKH-1003TKH-1042The iptables configuration now correctly blocks connections to the management ports (50022 and 50443) outside the whitelisted ranges.TKH-1004It is now possible to upload a certificate bundle as trusted CA.TKH-1006A configuration error could cause the installation to be blocked because of hidden buttons.TKH-1011It is no longer possible to configure the deployment mode via the appliance manager.TKH-1013The version of SaltStack is now managed by the appliance installer.TKH-1014The progress poller has been made much more resilient to network errors.TKH-1032Changing the maintenance password no longer requires a restart of Topicus KeyHub.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-885The Topicus KeyHub logos were replaced by SVG images.TKH-887A manager of an owning group can now directly add new groups to applications and linked systems.TKH-947A review was performed on correct validation of issuer and audience claims throughout Topicus KeyHub.TKH-949Measures have been taken to prevent a possible SSRF (Server Side Request Forgery) attack on the authorize endpoint, which could cause a Denial of Service.TKH-952The application server was upgraded to WildFly 13.TKH-953The web framework Wicket was upgraded to version 8.TKH-956Stronger input validation is applied to callback URIs for OAuth2 applications.TKH-957The code of OIDC flows with Topicus KeyHub as RP was rewritten to make it better maintainable.TKH-966Performance was improved for most of the authentication flows.TKH-973A sporadic error was fixed when performing re-authentication via OIDC.TKH-975The JDBC URL can now be configured on the application container, allowing more customized deployment of the database.TKH-977Copying the rotating password is now also handled by the browser extension.TKH-978Testing a connection to an LDAP now resets the internal connection pool.TKH-979Automatic grouping of elements is now performed case insensitive.TKH-984The browser extension no longer fills the username with 'undefined' on some pages.TKH-986Webhooks now support basic auth.TKH-987The event types vault record read and vault record deleted were switched when configuring webhooks.TKH-988The counters for selected event types were missing on Firefox when configuring webhooks.TKH-990Fetching a certificate from the server sometimes gave an error when configuring an LDAP directory.TKH-993Trying to register a new account when no directory exists gave an error.TKH-997The contents of a selected vault was not updated when a record was moved to a different vaultTKH-998Moving a vault record was not recorded in the audit log.TKH-999Copying the username of a vault record from the quicksearch on the dashboard no longer hides the other fields.TKH-1008The password is now displayed in a monospaced font when editing a vault record.TKH-1015Recovery of a nonexistent personal vault no longer gives an error.TKH-1020Registration of an internal account in maintenance mode no longer gives an error.TKH-1024The manual is now also available in English.TKH-1028Re-authentication via OIDC resulted in a Javascript error, rendering the return page partly unusable.TKH-1033Using square brackets in group names could cause errors on some pages.TKH-1035Resetting the password of an internal account no longer wipes the personal vault for that account.TKH-1036Invalid 2FA codes were recorded in the audit log twice.TKH-1038A request for resetting 2FA was erroneously denied when a request for a different account was not yet processed.TKH-1039The web session timeout was increased to 4 hours.TKH-1041Webhook deliveries are now removed after 2 days.

