We are pleased to announce the 11.1 release of Topicus KeyHub. In this release we enabled account provisioning on Windows servers and greatly extended the functionality of our built-in LDAP server. Furthermore we improved upon our automatic tests, fixed a few bugs and addressed some issues found in previous versions.
Windows account provisioning
TKH-774 TKH-773 A long held wish was finally realized with this release. We first improved our built-in LDAP server to be able to function as one or more linked systems. When a client application connects to the server it will see a dynamic view of active users and groups based upon which groups are active and how they are connected to the Internal LDAP the client is connected to.
This in turn enabled us to write a authentication plugin which uses this functionality to authenticate users on Windows servers, meaning that you can now login on Windows servers via Topicus KeyHub similar to how you could already login on *nix servers.
Automatic testing
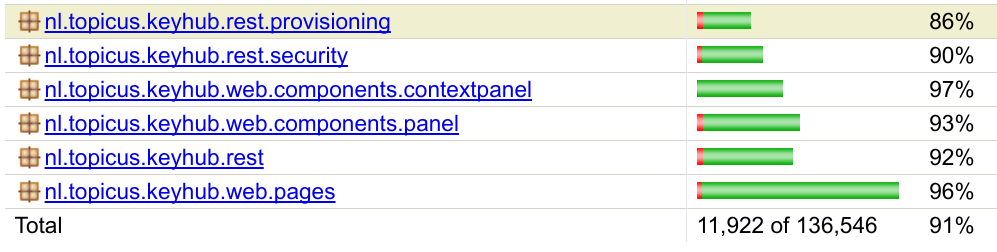
TKH-703 TKH-775 We parallelized our integration test suite earlier this year but in doing so we unfortunately lost our code coverage reports. The plugin we use to generate the coverage report was unable to handle multiple parallel runs in docker containers. We first fixed this issue by writing some wrapper code to gather and merge the coverage reports.
In the past few months we had dipped slightly below 90% coverage, mostly because of added functionality that we either could not test yet, such as the CLI, or that had not received enough attention. We first devised a way to test our Command Line Interface and ended up testing it from a selenium test suite running in docker containers. Next we worked through the coverage reports and looked at missed branches, methods or even complete classes to include in our testing.
In response to a few bugs we also implemented a way to test our delete calls by generating an extensively filled test-dataset, check it against the foreign-key references to ensure we filled everything, and then try to delete every deletable entity to ensure that we don't leave any dangling references which lead to errors.
The end result of all this work is a code coverage which is once again above 90%.
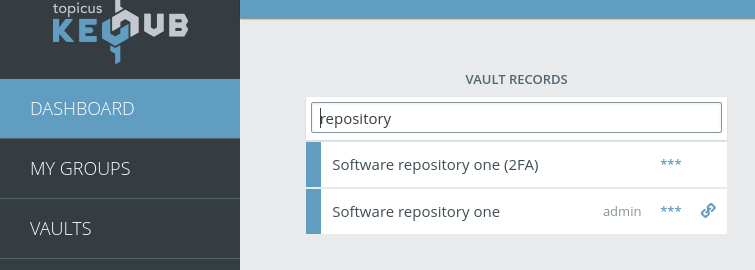
Quicksearch panel for vault records
TKH-772 In our ongoing User Experience interviews we learned that users who primarily use vaults are frustrated by the number of actions they have to perform to find and open a vault record. While a redesign of both the vaults page and the dashboard is in the works we added a small quality-of-life improvement. It is now possible to search for and open vault records directly from the dashboard.
Small improvements
The following smaller improvements and bugfixes were made:
TKH-488Changes in permissions now immediately take affect in the application.TKH-785We now register the uid of the provisioned account in the audit log to enable reverse lookups.TKH-776Audit records for deleted applications are now visible to the owning group.TKH-777Dates at the end of a year will no longer be rendered as with the next year.TKH-778Trying to open the browser extension when you need to re-verify your 2FA code will no longer result in an endless loop of password popups and "password incorrect" errors.TKH-780The graph on the statistics page once again show a limited number of 'ticks'.TKH-782We rewrote the indices on the audit log and limited the maximum age of the records shown on the dashboard to improve loading and searching speed.TKH-783You can once again enter a reason after clicking on an accept link in request-mailsTKH-787Clicking on the slider, instead of dragging and dropping the indicator, should once again work to choose an endtime for provisioning on Edge.TKH-788Opening a vault record when the vault is locked no longer results in double audit records.TKH-791Editing a directory should no longer result in an error page if the directory happens to be the default directory.

